2/7/19
I’m finding as I dig more and more into cybersecurity that there is a greater need to make sure DNS records are going to the forwarder that are specified in DNS, in this cause in a Windows Active Directory-based DNS.
If a user connects to the wireless as an example and they edit their DNS to something other than the one setup in DNS they could go to a place you don’t want them to go. So in order to prevent this and to use the forwarders set in Windows Server DNS, you got to setup rules to allow them and deny all the rest.
Below in a quick write up on how to do this:
Step 1:
First up you want to click on ‘Firewall’ in the ‘Protect’ Section, and then in the right side of the you want to click on the ‘Add Firewall Rule’ as shown below:

Step 2:
Then you want to setup the allow DNS rule. You setup the LAN as the source with any host and you set the destination as the WAN and you define the DNS records you have defined as your DNS forwarder in DNS such as Verizon FIOS and a 3rd DNS of your choosing for me I’m using L3 public DNS and then make sure you select the service of ‘DNS’ as shown in the picture below:
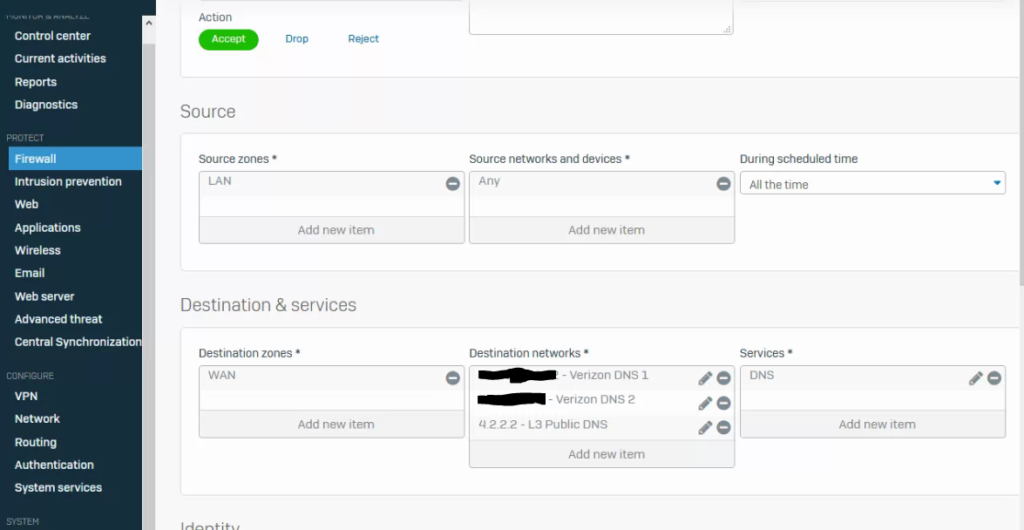
Step 3:
In this second to last step, you have to create a deny rule that blocks all of the DNs that isn’t defined in the allow rule. This is the one that blocks rogue DNS lookup to unknown DNS servers. Again, make sure you select the service ‘DNS’ as shown below:
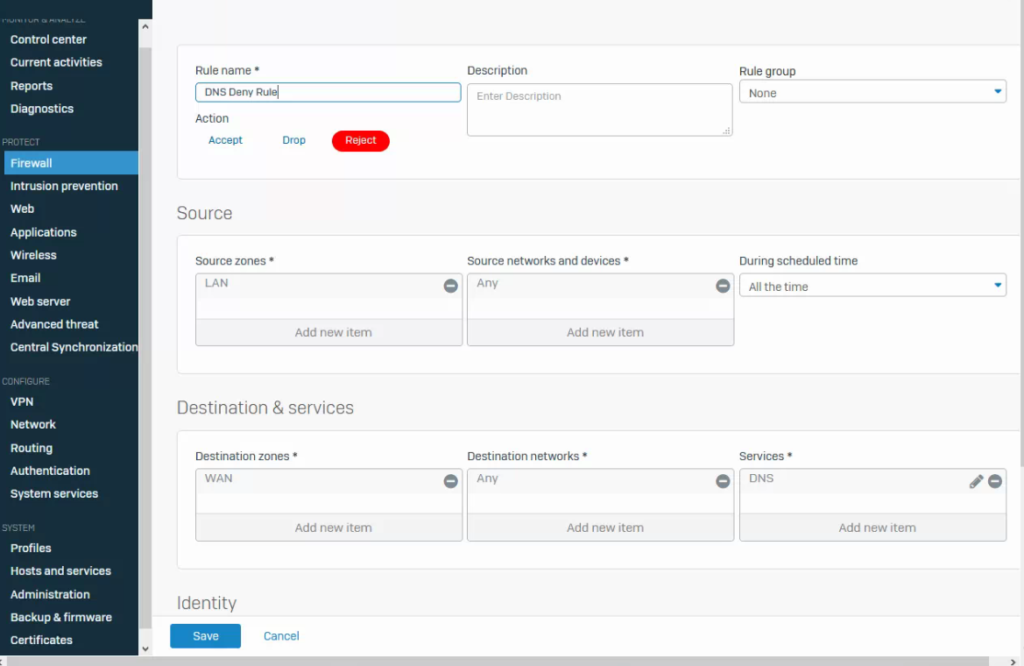
Step 4:
In the last step, navigate to the ‘Network’ sub-section under the ‘Configure’ section and click on the ‘DNS’ tab and make sure you have the Sophos firewall pointing toward the DNS server that is handling the forwarder DNS lookup (in this demo I’m just using one DNS server that is blacked out) so that your firewall knows where in send DNS lookup requests as shown below:
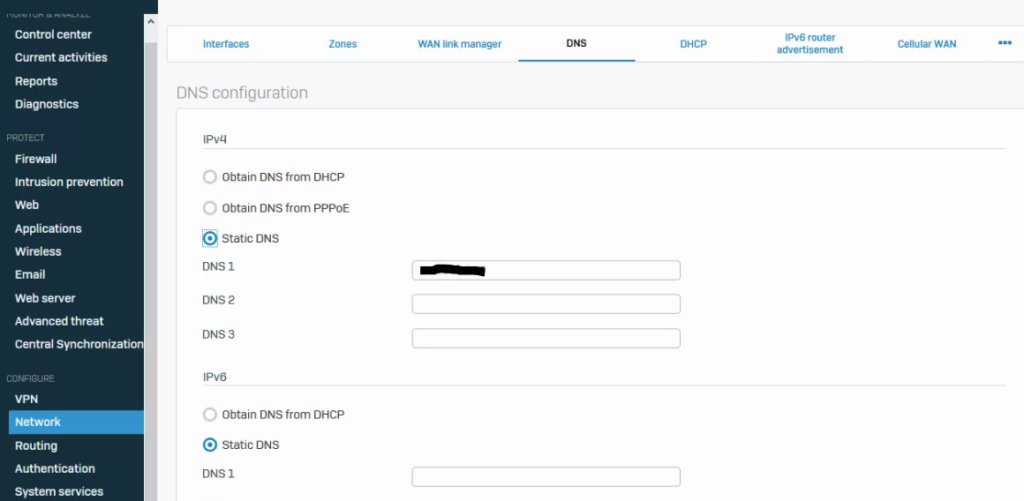
I hope this simple guide helps someone out and proves useful.
Cheers! 😀