9/21/19
Today discussion is around DNS Sockets and DNSSEC, two very important things I think all people should be aware of.
How many of you actually use DNS Sockets or know what they are?
DNS socketing provides greater protection from DNS spoofing, coupled with DNSSEC (also using a local PKI enhances this further, discussing PKI at length in a future article), it should allow for an enhanced secure DNS posture. 🙂
If you want to see how many your DNS server(s) are using type: “Get-DNSServer” in powershell, the default is 2500, however higher number increase the security of DNS.
Type the following command: dnscmd /config /socketpoolsize [0-10000]
Don’t forget to do a ‘net stop dns’ and a ‘net start dns’ or a reboot for this change to take effect. 🙂
On the flip side how many people actually sign the DNS for DNSSEC? – you should do it and then enforce all clients to use it. Note: it’s support with Windows 7 and above.
To enable DNSSEC, simply right click on the domain in DNS Manager and click DNSSEC > Sign the Zone. Make sure above all else you use a 2048 or higher key with at-least SHA-256 or higher. Don’t forget to activate DNSSEC for clients!
Open up the default domain policy: Computer Configuration> Policies > Windows Settings > Name Resolution Policy. The create a new rule and toggle the check box for ‘Enable DNSSEC in the rule’ and in the validation select ‘Require DNS clients to check that name and address data has been validated by the DNS Server’ and then press ‘create’ at the bottom. As Shown below:
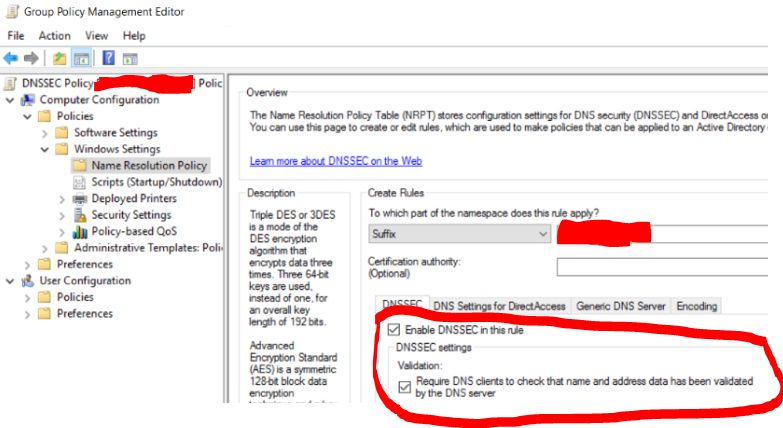
Don’t forget to do a gpupdate /force in elevated cmd on client desktops or you’ll have to wait 90 minutes for the GPO’s to poll and then since it’s a computer policy won’t take effect until the next reboot.
Also be aware if you are a Microsoft only network to use Secure only for dynamic updates and to make sure Zone transfers are for forest/domain NS only. 😀
NOTE: If you have non-domain workstations that connect to the domain, they will no longer be able to access resources.
Just wanted to share something we do, and wanted to make sure your all doing this. 🙂