4/6/19
We know about it, we all use it and we all assume it’s protected but is it truly?
RDP is the primary protocol of most organizations to allow remote access into a network, however there is a catch. The bad guys also know it’s being used so they make bots and scripts that scan this well known protocol and exploit it. You may be thinking, “I never thought of it like this” and my response would be “not many people do look at what in front of them and ponder this very obvious fact”. You may be asking what can I do about it?
Simple: change the port number!
But RDP uses 3389 and everyone knows this, my server can’t change this, right? – Wrong.
This port can be changed on the servers that allows RDP to connect to them and you can change your RDC client to point to this new port.
Now, yes, this won’t stop all of the attacks but most scripts and hackers look towards common ports and not high ports as scan that look for high ports take longer and risk being exposed in the process. It’s the traditional old saying “Security thru Obscurity” and this is how you do it:
- On the server in question you open up the registry in a elevated state and you navigate to the following hive location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp and look for a setting called “PortNumber” and it should be the default 3389, change this to a port above 1000 but below 64000; I’ve only tested to 64000. 😛
- For this demo I’ll change the port to 19891
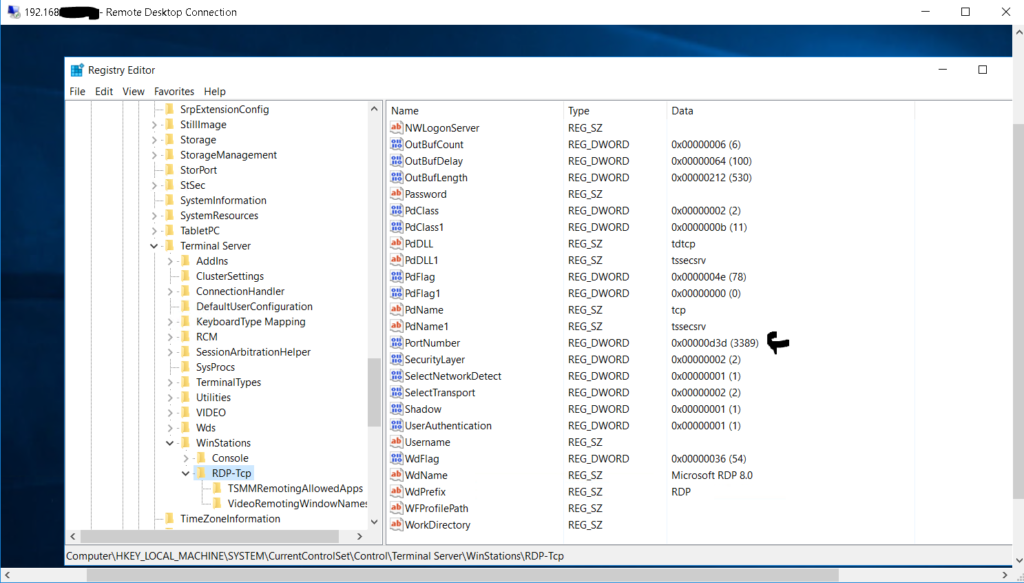
Now that we have done this, you can do the following:
2. Reboot the server
3. Open up your client machine and if you do this to a Terminal Server Farm, you’ll need to modify the RDP port of all RDC connections in the future
4. Below you can see in the RDC the address is set to 192.x.x.x:19891 and then you connect to the server.
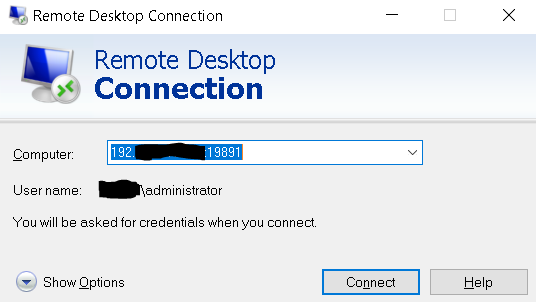
5. If you have remote users that connect to your RDP enable server or Terminal Server Farm you’ll need to modify your port forwarding rule to the new port number in order for remote sessions to be established.
I hope this quick write up on how to secure RDP is helpful to others and you implement this. This simple change won’t stop all APT-based attacks but it will help to mitigate most of them.
IT security is about constantly improving the process around “Defense-in-Depth” and I hope this topic helps you remember you should never take the obvious for granted and to question everything as that is what makes a IT professional one step ahead of the attacker.
Stay frosty, check your corners, and trust no one. 😛
Thank you for reading, Cheers!
~Trevor